Archive for the ‘Mobile App Management’ Category
Do you need a (new) mobile ecosystem?
Here at Moprise, we strongly believe that productivity and business need - including workflow, higher level application solutions, and services - dictates your back office computing infrastructure choices. One rarely selects a solution for mobile access alone. While mobile is important, a mobile-only blinder when making corporate infrastructure choices throws away years of experience, integration, and heavy lifting that got your company where it is. It’s important that your mobile strategy integrate with your existing corporate infrastructure.
Great coverage of this topic is written up by Brian Katz: http://www.ascrewsloose.com/2012/05/24/do-you-need-a-mobile-ecosystem/
Securing enterprise iOS devices - the new Apple Configurator
 Our customers want to have similar configurations across all their iOS (iPad & iPhone) devices. This includes settings like device PIN policies, iCloud backup or not, iCloud document sharing or not, WiFi setup including access point name and secret password, VPN setup including passwords and certificates, Exchange (or other email) server setup, and an initial set of corporate applications. Other stronger restrictions can be set if desired including disabling the ability to add apps, iTune user accounts, disable YouTube access, or even turn off the camera.
Our customers want to have similar configurations across all their iOS (iPad & iPhone) devices. This includes settings like device PIN policies, iCloud backup or not, iCloud document sharing or not, WiFi setup including access point name and secret password, VPN setup including passwords and certificates, Exchange (or other email) server setup, and an initial set of corporate applications. Other stronger restrictions can be set if desired including disabling the ability to add apps, iTune user accounts, disable YouTube access, or even turn off the camera.
The new Apple Configurator now available in the Mac App Store makes these basic tasks very easy and very repeatable, allowing an admin to give the device to a user and let them easily finish up the personal parts of the enrollment such as personal email address and passwords.
I was recently at the CITE conference (Consumerization of IT in the Enterprise) where BYOD in the enterprise was a key discussion topic. Distilling the best practices from the corporate discussions, the following three rules rise to the surface to ensure mobile device security:
1) Have a consistent PIN policy and utilize Exchange & Exchange Active Sync. This allows remote locking and remote wiping of devices.
2) Ensure employees report lost or stolen devices. When a device is lost, first lock the device remotely to give the employee a chance to find it. After a few days, remote wipe the device to protect corporate & personal assets. A remote lock and then a remote wipe encourages people to report lost devices sooner than later as it allows employees time to find them. These remote locking & wiping features are available via Outlook Web Access as discussed in an earlier post so employees could take these precautions themselves.
3) Have employees sign an agreement that ensures they & you follow these guidelines when using a mobile device for work. This ensures you have permission to erase their device and they understand you are balancing corporate security with preservation of their personal data.
Apple’s new Configurator makes rolling out iOS devices easy and if you don’t have a Mac in your corporation, buying one simply to use the Configurator will save you significant time and effort ensuring a consistent iOS security profile across all your users.
Trialing iPads: Protect Corporate Data Using Free Microsoft Exchange Mobile Device Management
We regularly work with IT leaders or users who are doing trials of iPhones and iPads within their corporations. These devices come into the corporate in an ad hoc fashion as employees, CxOs, and departmental heads experiment with them as they formulate opinions around use cases and potential business productivity gains.
Experiments begin by connecting to the two enterprise staples: email & storage. Using the Exchange support built into the iPhone/iPad email client, users connect to Microsoft Exchange for email and using our free Moprise for SharePoint product, they connect to SharePoint servers.
 After a few minutes, visions of productivity improvements for field service teams getting remote access to repair manuals, customer appointment schedules, and tier 2 experts come into people’s heads. Or, by using Coaxion, the ability for the corporate board of directors to conduct paperless meetings using an iPad portfolio containing strategic documents from department heads, links to live performance indicators, and contact info in preparation for, during, and post a meeting.
After a few minutes, visions of productivity improvements for field service teams getting remote access to repair manuals, customer appointment schedules, and tier 2 experts come into people’s heads. Or, by using Coaxion, the ability for the corporate board of directors to conduct paperless meetings using an iPad portfolio containing strategic documents from department heads, links to live performance indicators, and contact info in preparation for, during, and post a meeting.
Very quickly, a few hundred megabytes of email and documents find their way onto devices in these ad hoc trials. And now the pragmatic realities of what happens if this device is lost or stolen fall into people’s minds.
Luckily for us, Apple and Microsoft cooperated to put device management capabilities into Exchange server and iOS (iPad/iPhone) devices. In a worst case scenario, a user or IT administrator would be able to remote wipe an iOS device using Microsoft Exchange’s device management capabilities. A real world deployment may need more sophisticated device and application deployment and configuration capabilities, but for early trials, the built in support from Microsoft Exchange addresses many worst case nightmares. This allows leaders and end users to evaluate the real productivity gains possible from enterprise apps without compromising corporate IP.
While Apple’s MobileMe offers similar “find my phone” and “remote wipe” capabilities, this is only available to the AppleID user. Exchange Mobile Device Management capabilities can be accessed by both the end user and trusted IT professionals which allows for proactive protection of corporate assets.
 To access the device management capabilities of Microsoft Exchange, you will need to log into Outlook Web Access. After logging in, you will see an “options” menu item on the right side of the web page. Select “options” and the “see all options” setting to bring up the full list of Exchange/Device Management capabilities.
To access the device management capabilities of Microsoft Exchange, you will need to log into Outlook Web Access. After logging in, you will see an “options” menu item on the right side of the web page. Select “options” and the “see all options” setting to bring up the full list of Exchange/Device Management capabilities.
—-
 You should then select the “phone” tab to see the list of devices including the ability to wipe the full device. Statistics on the device including when it was last used are also available in case stronger precautions need to be taken.
You should then select the “phone” tab to see the list of devices including the ability to wipe the full device. Statistics on the device including when it was last used are also available in case stronger precautions need to be taken.
-
-
-
-
-
-
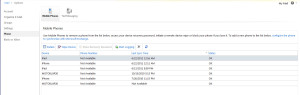
This web page (click the image to enlarge) shows you all your individual phones and tablets that have connected to the Exchange server, the last time they sync’ed, and a button to wipe the device. Here you see the iPads, iPhones, and Android devices that have hooked up to my Exchange email account, all easily managed in case the worst happens.
Two urls from Microsoft provide background on the supported devices and the feature set for Exchange device management. You may want to share these with your IT team in case they have questions around the security of your experiments in mobile productivity.
An overview of cross platform mobile device management via Exchange: http://blogs.technet.com/b/uc/archive/2011/04/13/mobile-device-management-just-got-easier-announcing-the-exchange-activesync-logo-program.aspx
A list of supported devices & management capabilities: http://technet.microsoft.com/en-us/exchange/gg187968.aspx
iCloud and the Enterprise
We’re at WWDC this week and the biggest announcement from Apple was iCloud. iCloud is a free Apple service that ensures your personal data is wirelessly synchronized to the cloud, your iOS devices, PCs, and Macs.
Data automatically going somewhere is a legitimate concern for an enterprise. Lots of questions come to the surface - how is it shared, who has access to it, what controls are there, who is in control, and many more.
The concern for data sharing
Corporations have spent billions storing, securing, archiving, and managing corporate data in systems like Exchange, Oracle, File Servers, SharePoint, EMC Documentum, and IBM FileNet. There are compliance checks and data retention policies on who accesses it and how its shared. IT has controlled how this data gets onto PCs via Outlook and onto devices via email clients and applications like our Moprise for SharePoint iPad application. iCloud introduces some obvious concerns with the automatic propagation of corporate data into Apple’s cloud, onto other devices, and the possible co-mingling of personal & corporate data.
The scope of iCloud
Personal - From the Apple keynote, iCloud is currently designed for synchronizing data across devices linked to a specific Apple ID. This means devices registered by a particular Apple ID will automatically be synchronized. Some families share Apple IDs so that the same music and movies are available to everyone and in these scenarios iCloud data would be synchronized across all devices. To keep your data private, you should not share devices and Apple IDs with others.
Per Application - Each application decides how it uses iCloud synchronization APIs and what data is copied into the cloud. Some (all?) of the Apple supplied applications - the iWork suite was demonstrated during the keynote - utilize iCloud. This means data shared with these applications is subject to synchronization into the cloud. For example, a corporate application that uses “open in” to view a document in Pages, could have the document synchronized into the cloud and onto other devices. We will need clarity on how email configuration and email itself is synchronized to other devices. Corporations may not want Exchange email automatically showing up on rarely used personal devices but it could be useful to easily share the configuration between a frequently used iPhone and iPad.
Per Device Back Up - Today, each time a device is plugged into iTunes, a backup is automatically created of all the state on the device. This should be encrypted if corporate data is stored on the device. But in the future, with iCloud, a backup to the cloud will automatically be created. Is this automatically encrypted? Can this be disabled?
Key Chain - User names and passwords are stored into the key chain for secure access by applications. This useful feature enables onclick login to websites or servers without fear of someone stealing the cached password. But synchronizing this information onto lost or rarely used devices would be a concern.
Configuration Profiles - A corporation may install configuration profiles on a device that control policies, set VPN certificates, and other lock down state on the device. Understanding how this is synchronized to other devices will need to be made more transparent.
What controls are needed?
Corporate Configuration - Any “corporate owned” data and configuration clearly needs independent controls on how it should be propagated into iCloud and synchronized across devices. Enterprise certificates, VPN configuration, and Exchange configuration, at the very basic, need controls to disable automatic sharing across personal devices.
Enterprise Applications - Enterprise applications already need to be designed with features like security, encryption, and data protection in mind. Enabling controls and sensible defaults around how their documents and settings are copied to the cloud will also make sense. In most cases, additional copies of corporate data outside of corporate storage systems won’t make sense.
Corporate Documents - Documents sent via email and Moprise or Coaxion SharePoint documents can be opened in productivity applications like iWorks for editing or viewing. Documents passed between applications need an attribute that indicates to the iCloud apis they should not be synchronized into iCloud and across devices. The document file itself would hold the attribute so it survives as it is copied between apps. This would allow corporate documents to be used by iCloud enabled applications yet still preserve any corporate security decisions. Corporate apps would need to change to add this attribute but other apps do not need any changes - meaning only the apps that get value from the security need to change.
Next Steps
As consumers with multiple devices, iCloud solves lots of challenges and we welcome the ease of moving between our devices seamlessly. As well, the value provided by cloud synchronization and sharing will get greater over time as other companies like Microsoft also embrace cloud documents. As a producer of broadly used enterprise applications, we get lots of feedback from IT and CxOs on the security and integrity of corporate data brought to devices. At Moprise, we will continue to dive into the iCloud APIs and documentation provided by Apple and provide feedback on what we need to tune our enterprise applications to secure corporate IP and promote productivity across mobile devices.
Taking Your New iPad 2 to Work: Mission Impossible?
http://gigaom.com/apple/bringing-your-new-ipad-2-to-work/
Over at GigaOm, you’ll find a basic article on how to configure your new iPad 2 for work. They echo the IT trend of “bring your own everything”, including your iPad, to work. However, the article is clearly small business focused as they assume it is generally easy to connect to secured WiFi networks via hand typed passcodes and the apps recommended exist in silos, independent of the knowledge contained within your corporation.
For enterprise users, installing certificates for enterprise WPA2, IPSEC, or even secure VPN access is mission impossible unless you have help from your IT department. Apple provides instructions for IT Departments to provision servers to deploy these certificates and to configure VPNs to automatically start when corporate URLs are used, but in many cases these servers aren’t deployed or aren’t accessible to personal devices. In some enterprises, you can find a local user group or email alias that helps new Apple users get their devices hooked up to their enterprise infrastructure. In others, you are still out of luck connecting to the enterprise network.
Adding an Exchange account to your iPad or iPhone is easy but you need to remember you have implicitly given your IT department permission to wipe your entire device if it gets lost or if you leave your job. Make sure you back up often by connecting to iTunes. Additionally, your Exchange server can force a PIN code to access your device for your personal data in addition to your corporate Exchange email which can get in the way of quick access to your phone.
We still see there’s a long way to go before personal devices are safe and usable for work in the enterprise. The big problems we see are:
1) Connecting to the enterprise network and enterprise infrastructure
2) Finding and connecting to your co-workers
3) Ensuring corporate apps & data are protected and controlled by your corporation
4) Ensuring your private apps & data remains private and controlled by you
At Moprise, we’re working towards empowering users with the apps they need to make personal devices in a corporate world actually work. We will empower users with the apps they need to route around the impediments and get work done. Our free iPad and iPhone apps enable anyone to access SharePoint and were our first steps in unblocking user productivity.
Stay tuned for an exciting new set of apps & services that will be a tremendous advance in how enterprise users connect and collaborate.
Follow us @moprise to keep in touch.
Personal Phones in the Enterprise - Who is In Charge?
Many corporations are selecting mobile device management technologies to configure and manage phones in the enterprise. Mobile device management technologies provide a detailed view of the phone including what calls were made, what apps were installed, what data is on the phone, and who the carrier is. Additionally, it can impact the operation of the phone by allowing or blocking apps, forcing passwords, sharing the location of the device, and allowing for data wipe, backup, and restore. This is a rich set of functionality which allows corporate IT to ensure your phone works, help you trouble shoot issues, and preserve the integrity of their intellectual property in a robust way.
Unfortunately, a mobile device management strategy neglects the smartphone user’s right to privacy especially in today’s world where we use our personal phones for work. Should corporate rules against social networking sites apply to your personal phone? Does your personal data become viewable and usable by the corporation because they backed it up? Are your phone calls automatically subject to scrutiny by corporate HR? Using a personal phone for work ensures you are readily reachable and connected to your work place. Your ability to utilize the device for productive work across email and apps dramatically increases. The employee paying the cost of the device and cellular plan reduces the overall expenses of the corporation. In exchange for these benefits, the corporation must respect the phone owner’s rights while ensuring the corporate specific settings and apps are protected.
The obvious solution to this is moving from mobile device management (MDM) to mobile application management (MAM), where manageability occurs at the application level. This allows corporate applications to be managed, authorized, and monitored independently of other applications on the device. In essense, there should be a strict partitioning between apps from my corporation and my personal apps.
This means consumer applications cannot interfere with managed corporate applications. And unmanaged or unapproved corporate applications cannot access corporate networks and infrastructure or other corporate applications. The curated Apple App Store seems to ensure applications are well behaved and inherently isolated from each other. The less managed Android store seems to have a greater preponderance of malware which requires a stronger technical solution like a hardened sandbox before it is acceptable to corporate IT.
We think a mobile application management solution will enable both personal and corporate worlds - I will be in charge of my phone and applications and my corporation can feel comfortable I’m adhering to their standards with their apps.