Archive for the ‘security’ Category
Securing enterprise iOS devices - the new Apple Configurator
 Our customers want to have similar configurations across all their iOS (iPad & iPhone) devices. This includes settings like device PIN policies, iCloud backup or not, iCloud document sharing or not, WiFi setup including access point name and secret password, VPN setup including passwords and certificates, Exchange (or other email) server setup, and an initial set of corporate applications. Other stronger restrictions can be set if desired including disabling the ability to add apps, iTune user accounts, disable YouTube access, or even turn off the camera.
Our customers want to have similar configurations across all their iOS (iPad & iPhone) devices. This includes settings like device PIN policies, iCloud backup or not, iCloud document sharing or not, WiFi setup including access point name and secret password, VPN setup including passwords and certificates, Exchange (or other email) server setup, and an initial set of corporate applications. Other stronger restrictions can be set if desired including disabling the ability to add apps, iTune user accounts, disable YouTube access, or even turn off the camera.
The new Apple Configurator now available in the Mac App Store makes these basic tasks very easy and very repeatable, allowing an admin to give the device to a user and let them easily finish up the personal parts of the enrollment such as personal email address and passwords.
I was recently at the CITE conference (Consumerization of IT in the Enterprise) where BYOD in the enterprise was a key discussion topic. Distilling the best practices from the corporate discussions, the following three rules rise to the surface to ensure mobile device security:
1) Have a consistent PIN policy and utilize Exchange & Exchange Active Sync. This allows remote locking and remote wiping of devices.
2) Ensure employees report lost or stolen devices. When a device is lost, first lock the device remotely to give the employee a chance to find it. After a few days, remote wipe the device to protect corporate & personal assets. A remote lock and then a remote wipe encourages people to report lost devices sooner than later as it allows employees time to find them. These remote locking & wiping features are available via Outlook Web Access as discussed in an earlier post so employees could take these precautions themselves.
3) Have employees sign an agreement that ensures they & you follow these guidelines when using a mobile device for work. This ensures you have permission to erase their device and they understand you are balancing corporate security with preservation of their personal data.
Apple’s new Configurator makes rolling out iOS devices easy and if you don’t have a Mac in your corporation, buying one simply to use the Configurator will save you significant time and effort ensuring a consistent iOS security profile across all your users.
Secure business and personal apps with iOS
Today another new Android vulnerability was discovered such that all your email addresses, phone numbers, SMS messages, and log files can be access by any application that requests permission to access the internet. You can read more about it here. Additionally there has been android malware in the Marketplace that captures and reroutes your personal data to 3rd parties.
It’s useful to ask why Apple’s iOS doesn’t face similar threats. I think there are three reasons for this:
1) With the Macintosh, Apple differentiated itself from Windows by claiming there were no viruses or malware on its platform. This feature resonated with customers in a big way and Apple knew it must carry this forward. However, in the PC era, Mac’s malware resistance really was just marketing. As Apple thought about new models for computation, they realized strong technical firewalls would be needed to more fundamentally prevent these threats from harming users.
2) iOS has a curated application store with very end-user favorable rules that app developers must follow such as not using undocumented apis. Apps are actively scanned for viruses and malware behavior before they can get into the store. If a bad app ever leaks into the store, Apple has the technology to remove an offending app from the store and from devices before it infects everyone. As this is the only path for getting apps onto devices, Apple is like a bouncer at the bar actively keeping unwanted apps out while ejecting misbehaving apps that got in.
3) iOS has a very strong sandbox between apps and a very rigorous api that prevents applications from interacting or sharing data with each other except through a very few well protected apis. First, unlike Android, an application cannot access the code or data of another application. All sharing is done via a few well-defined iOS apis – so there is a spigot and drain approach to sharing that is controlled by the app, the user, and the OS. It is iOS that prompts you before sending email, making a phone call, or sharing a document between applications so that even allowed commands require user confirmation.
With these technologies, business apps can co-exist side by side with consumer apps on the phone. iOS guarantees the business apps cannot be accessed or changed by any other application on the phone. As well, your personal apps & data are safe from corporate scrutiny. In addition, via iOS apis, the business apps can limit their data sharing to other trusted business apps and recently introduced AppConnect technology from Mobile Iron appears to be a start in this direction.
The iPhone & iPad truly have the fundamentals to support one device that delivers work and personal utility while balancing the security and privacy needs for both sides of our lives. Ray Ozzie captured a good summary of iOS a few years ago: Apple internalized that people really understand and like an appliance-style model for their phone & pad. Appliances don’t get viruses, they don’t data share, they do one function and do it well.
Setting Up Moprise for the iPad
Many of you are familiar with Moprise for the iPad. Moprise is our SharePoint viewer that allows you to access, pull, and email documents to create a magical iPad experience that is easy for users and requires no training. Moprise also saves you time by only requesting your SharePoint log in credentials once. Moprise is also secure.
We’ve released a getting started video! What is your SharePoint URL? Where do you get it? How do you pull documents to work on them? What programs can you pull documents into? Our video will walk you through, and give you a preview of what you’ll see in Moprise if you haven’t downloaded it yet. Enjoy!
The Dropbox Blackbox Part 2
Previously we wrote about the password-optional flaw in Dropbox.
Today, new information from Dropbox tells us that less than 100 accounts were accessed, the impacted Dropbox account users informed, and hopefully the single individual who discovered the hole and exploited the accounts will face some consequences.
Unless we’re one of the unfortunate 100, we can remove this worry from our list.
Trialing iPads: Protect Corporate Data Using Free Microsoft Exchange Mobile Device Management
We regularly work with IT leaders or users who are doing trials of iPhones and iPads within their corporations. These devices come into the corporate in an ad hoc fashion as employees, CxOs, and departmental heads experiment with them as they formulate opinions around use cases and potential business productivity gains.
Experiments begin by connecting to the two enterprise staples: email & storage. Using the Exchange support built into the iPhone/iPad email client, users connect to Microsoft Exchange for email and using our free Moprise for SharePoint product, they connect to SharePoint servers.
 After a few minutes, visions of productivity improvements for field service teams getting remote access to repair manuals, customer appointment schedules, and tier 2 experts come into people’s heads. Or, by using Coaxion, the ability for the corporate board of directors to conduct paperless meetings using an iPad portfolio containing strategic documents from department heads, links to live performance indicators, and contact info in preparation for, during, and post a meeting.
After a few minutes, visions of productivity improvements for field service teams getting remote access to repair manuals, customer appointment schedules, and tier 2 experts come into people’s heads. Or, by using Coaxion, the ability for the corporate board of directors to conduct paperless meetings using an iPad portfolio containing strategic documents from department heads, links to live performance indicators, and contact info in preparation for, during, and post a meeting.
Very quickly, a few hundred megabytes of email and documents find their way onto devices in these ad hoc trials. And now the pragmatic realities of what happens if this device is lost or stolen fall into people’s minds.
Luckily for us, Apple and Microsoft cooperated to put device management capabilities into Exchange server and iOS (iPad/iPhone) devices. In a worst case scenario, a user or IT administrator would be able to remote wipe an iOS device using Microsoft Exchange’s device management capabilities. A real world deployment may need more sophisticated device and application deployment and configuration capabilities, but for early trials, the built in support from Microsoft Exchange addresses many worst case nightmares. This allows leaders and end users to evaluate the real productivity gains possible from enterprise apps without compromising corporate IP.
While Apple’s MobileMe offers similar “find my phone” and “remote wipe” capabilities, this is only available to the AppleID user. Exchange Mobile Device Management capabilities can be accessed by both the end user and trusted IT professionals which allows for proactive protection of corporate assets.
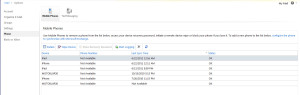
 To access the device management capabilities of Microsoft Exchange, you will need to log into Outlook Web Access. After logging in, you will see an “options” menu item on the right side of the web page. Select “options” and the “see all options” setting to bring up the full list of Exchange/Device Management capabilities.
To access the device management capabilities of Microsoft Exchange, you will need to log into Outlook Web Access. After logging in, you will see an “options” menu item on the right side of the web page. Select “options” and the “see all options” setting to bring up the full list of Exchange/Device Management capabilities.
—-
 You should then select the “phone” tab to see the list of devices including the ability to wipe the full device. Statistics on the device including when it was last used are also available in case stronger precautions need to be taken.
You should then select the “phone” tab to see the list of devices including the ability to wipe the full device. Statistics on the device including when it was last used are also available in case stronger precautions need to be taken.
-
-
-
-
-
-
This web page (click the image to enlarge) shows you all your individual phones and tablets that have connected to the Exchange server, the last time they sync’ed, and a button to wipe the device. Here you see the iPads, iPhones, and Android devices that have hooked up to my Exchange email account, all easily managed in case the worst happens.
Two urls from Microsoft provide background on the supported devices and the feature set for Exchange device management. You may want to share these with your IT team in case they have questions around the security of your experiments in mobile productivity.
An overview of cross platform mobile device management via Exchange: http://blogs.technet.com/b/uc/archive/2011/04/13/mobile-device-management-just-got-easier-announcing-the-exchange-activesync-logo-program.aspx
A list of supported devices & management capabilities: http://technet.microsoft.com/en-us/exchange/gg187968.aspx
The Dropbox Blackbox
Dropbox was password optional for four hours…
With 25 million users and a gazillion files, from a consumer perspective, I and many others can’t live without Dropbox. Even Microsoft’s latest update to Skydrive doesn’t help because it isn’t cross platform like Dropbox. And even then, it isn’t 10x better than Dropbox and I already pay for Dropbox, meaning it is unlikely I would switch. So when I heard about the latest Dropbox issue where passwords were inadvertently disabled for a four hour period, I was concerned about my files & documents and could make a decision on behalf of my family to stay or go somewhere else. Note, we’re staying with Dropbox.
However the latest breech of Dropbox potentially exposed critical corporate data stored by individual users. This could now be cached in search engines or accessed by hackers trolling for open shares and is now stored somewhere even after the bug has been fixed. The implications of exposed corporate data really need to be understood and mitigated by senior IT and corporate leaders - customers, shareholders, and the corporation itself could be exposed.
Had this been a corporate storage system, logs would be used to inform corporations of files accessed during the window of vulnerability. This would allow corporations to take precautions including notifying customers of any information disclosure. Unfortunately, being a consumer system, Dropbox doesn’t offer this service. And if it did, employees would need to inform their IT departments independently. Additionally, a careful IT Department has no idea what its employees have stored on Dropbox so precautions cannot be taken. All we can do is cross our fingers.
Dropbox is an IT blackbox. This is why corporations invested in their own storage systems or they purchase enterprise grade cloud storage where precautions are taken and in case of failure, the value of timely notification is standard operating procedure.